Uniting Identity Lifecycle Management, Governance, Access Control, and Threat Detection – All in One Seamless Solution
Top Identity Security Challenges – and How We Help Turn Them into Wins
Fragmented systems reduce clarity into identity access and risk exposure.
Centralized, real-time monitoring delivers complete visibility across all identities and entitlements
Different systems don’t always work well together, making security hard to manage.
Manual processes and scattered tools slow you down and increase costs.

Conversations at the intersection of identity, cybersecurity, and business strategy, designed for leaders navigating an evolving threat landscape.
We Bridge Your Identity Security the Best
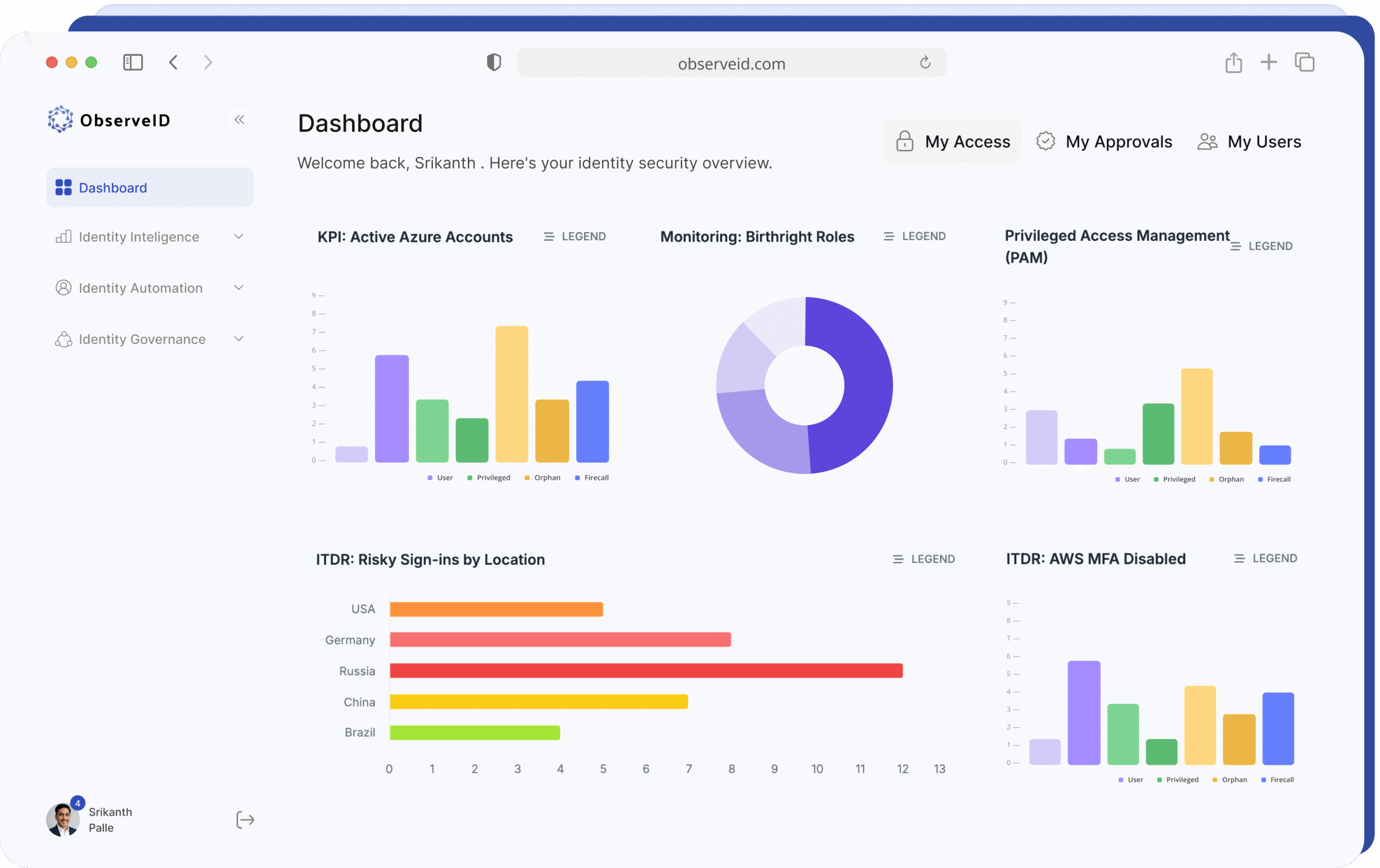
Complete identity security, all in one place - IAM, IGA, PAM, CIEM, and 360-degree visibility
Compliance reports covering security standards and regulatory requirements
Visual dashboards, unified profiles, automated workflows, and report generation
Simple, efficient, cost-effective, and built for impact
Seamless Integration with your existing systems
Continuous monitoring, real time threat detection & automated response.
On-premise or cloud, with legacy systems or standalone
AI-assisted for UAR and role Mining
Your Identity Security Needs to Think Ahead – We Bring Automation, Intelligence, and Governance Together
Choose Better Operational Efficiency
Automating key tasks ensures your security is always in the right place, with the right person at the right time.
Choose Better Security Posture
AI-powered intelligence stays one step ahead, spotting user behaviors, risks and guiding smarter security that is proactive.

Choose Compliant Regulatory Requirements
Governance ensures the right permissions at the right time through automated policy enforcement and real-time monitoring. Keep your audits ready with continuous compliance.
A Bridge Built with Trust, Secured by Outcomes
“In regards to the support, I have confidence on the team expertise on IGA platforms and best practices. They have provided us with support and help to overcome issues even if it’s not directly caused by the platform.“
Information Security Infrastructure Specialist, BUPA
“ObserveID gives us clear visibility into user activity, consolidating steps into one view to make security monitoring faster, easier, and more reliable.“
Sr. Information Security Analyst, ESS, Inc.
“Working with ObserveID has been a game-changer. Their intelligent automation, streamlined orchestration, and their deep domain expertise in identity security, combined with a team that truly knows their stuff and always has our back, make them an incredible partner.“
President, GPL Solutions LLC
Data fabric technology easily connecting cloud, hybrid and on-premises infrastructures with 100s of connectors allows for 360º visibility

You’re Not Just Onboarding a Platform, You’re Partnering With a Team That Goes the Extra Mile