Achieving visibility is the key to successful identity management
In the world of cybersecurity, visibility is a term often mentioned, but never fully defined. After all, what is visibility in the context of protecting organizations from compromises? When it comes to Identity Management, visibility takes on a new meaning – one that conceptualizes the ability to view all the metadata around an identity.
Simply put, identity management is much more than just name, location, and other arbitrary data field. Without knowing and understanding elements such as access permissions, entitlements, authorized applications, and so on, identity management proves virtually worthless, at least in the context of cybersecurity.
Managing user identities is challenging
Further complicating these issues is the simple fact that a user, whether human or machine, may have numerous identities spread among multiple cloud or on-premise services. What’s more, many of those user directories (or account identity providers) lack the tools to report the metadata surrounding a particular identity. This means that even if IT security administrators know some or all the identities and basic facts surrounding a user, they may have little or no understanding of what permissions are assigned, inherited, or shared. A conundrum that leaves those responsible for cybersecurity in the dark.
This lack of visibility makes organizations very vulnerable to cyberattacks, such as account takeovers, escalated privileges, eavesdropping, ransomware, password attacks, or other malicious surface attacks. In those instances, visibility becomes a primary tool to ascertain risk and mitigate threats.
Typically, today’s threats leverage common weaknesses found in digital identities, such as lack of proper management, poor policies, weak passwords, and over privileged rights, most of which are caused by how identities are provisioned, managed, and secured. With that in mind, those responsible for cybersecurity must garner enough knowledge of identities to analyze potential threats. However, this task is almost impossible with siloed identity management systems.
Breaking down the identity management siloes
So, the question becomes, “how can IT security administrators get the full picture of what an identity means and how it impacts access to resources?”
The first step to addressing that question comes in the form of unified identity management, which can gather information from multiple silos and then present that information in a central dashboard. What’s more, that dashboard should be able to correlate account information across identity silos and present it in a unified fashion. Yet, that alone does not resolve all of the issues around identity management.
Administrators need to take several more steps to gain control of identities and entitlements. Improved visibility is just the first step, other steps include analysis of accounts, analysis of entitlements, and the establishment of policies. Tasks today that tend to be beyond the manual controls and systems included with siloed directories. What’s more, as enterprises embrace more services and leverage the cloud, the concept of a centralized identity has become an artifact of the past.
Minimizing Insider Threats
While external security risks often grab the spotlight, internal threats pose a significant danger to an organization. Insider threats can stem from intentions or even simple oversights like employees inadvertently exposing sensitive data. Identity and access management (IAM) systems play a role in reducing the risk of insider threats by closely monitoring and recording user actions, enabling prompt detection and response to suspicious behaviors. By implementing access controls and regularly reviewing permissions, organizations can ensure that employees have access only to the data required for their specific roles. This proactive approach helps mitigate the chances of both misconduct and unintentional data breaches.
Enhanced Cost Effectiveness
Efficient IAM implementation can result in cost savings for organizations. Automating user access management alleviates the burden associated with manually handling user identities and access rights. This not only saves time but also decreases the likelihood of errors that could lead to security vulnerabilities. Furthermore, IAM plays a role in reducing the risk of security incidents that may incur significant remediation costs. For instance, data breaches can result in financial losses due to expenses related to legal matters, regulatory penalties, and harm inflicted on an organization’s reputation. By averting incidents through effective IAM strategies, organizations can steer clear of these expenses and allocate resources more effectively.
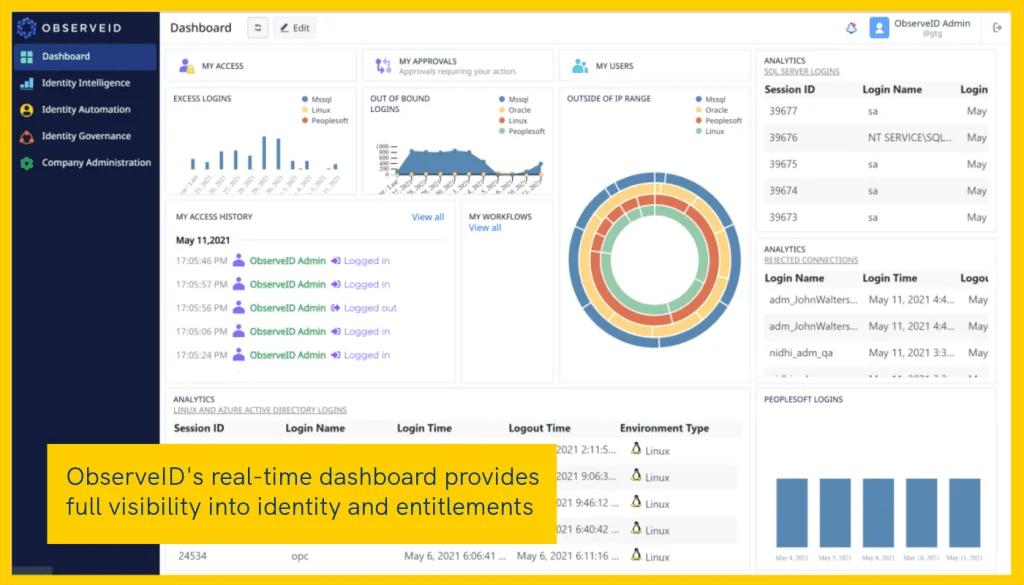
As environments grow in complexity, businesses will need advanced tools, along with automation to garner the visibility required to act on actionable information about accounts, identity, and entitlements. Requirements that shout for the need of more than just an IAM (Identity and Access Management) Platform. Full visibility can only be accomplished by establishing identity intelligence, backed by automation and real-time scanning.
For example, the ObserveID platform supports hybrid and multicloud environments and centralizes identity management chores, while also monitoring identity behaviors, determining access patterns, and correlates access activity into an analytical dashboard. In other words, ObserveID gives full visibility into identity and entitlements.
What’s more, ObserveID goes beyond the capabilities of the typical IAM and incorporates advanced analytics, which can reveal additional information related to account provisioning. Visibility proves critical for properly governing identities and accounts across multiple applications and clouds.
Enhanced Cost Effectiveness
Overall, visibility helps bring additional value to user account and identity management by establishing an all-important “truth” about accounts and entitlements. That centralized concept of truth helps to smooth over provisioning tasks and creates the foundation to discover potential cybersecurity threats.
While many organizations turn to IAM tools to ease the burdens of account and entitlement management, it is critical to understand that if those platforms do not provide full visibility or incorporate automation, then those organizations are setting themselves up for potential failure when it comes to cybersecurity.
